Have any questions?
+44 1234 567 890
IT Compliance
IT compliance includes in particular the protection of IT systems against attacks from inside and outside. For this purpose, the Center for Internet Security (CIS) provides benchmarks with detailed instructions on how to secure IT systems. Benchmarks are available for all common operating systems and software.
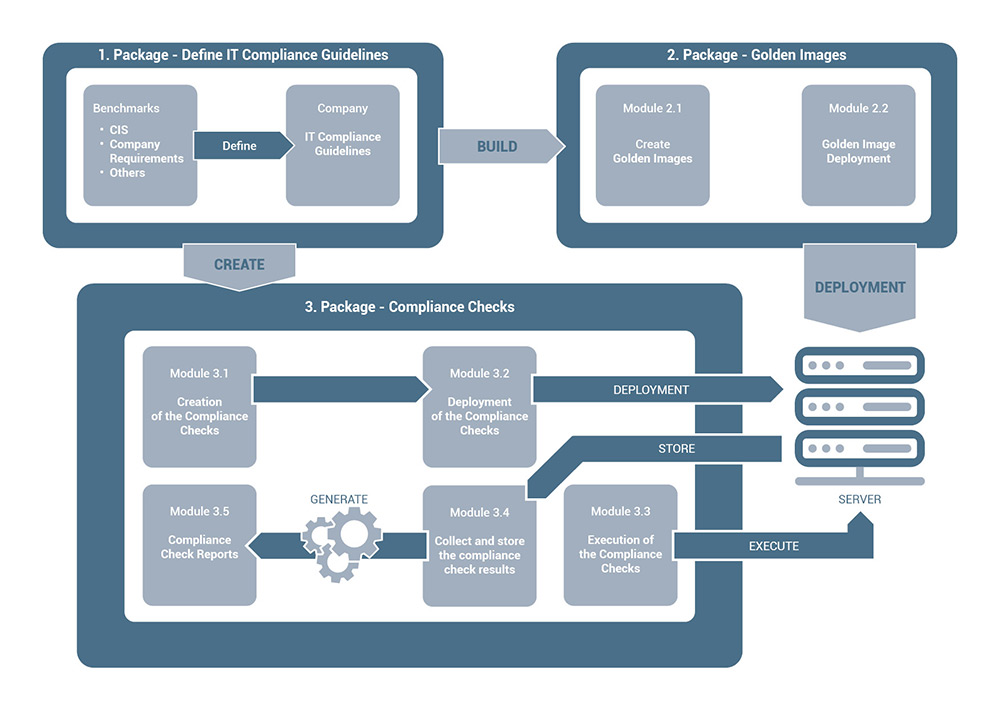
We check and harden your IT systems according to CIS security standards or our own compliance rules. For this we offer 3 packages with several modules, which you can book as a complete package or individually. Every single package and module can be adapted to your own wishes.
Based on CIS benchmarks and your own requirements, we create your corporate compliance guidelines for all security-relevant IT systems in your company.
Module 2.1 – Create Golden Images
Based on the compliance guidelines from package 1, we create so-called golden images, i.e. hardened images of your software. The golden images are created in the target formats you require, such as zip, tar, docker, rpm and many more.
Module 2.2 – Golden Image Deployment
Some compliance policies can only be implemented during deployment, e.g. because file directory rights must be set. For this purpose, we offer you predefined automated deployment procedures for your applications, e.g. with Ansible.
Module 3.1 – Creation of the Compliance Checks
Based on the compliance guidelines from package 1, we create scripts to check the compliance guidelines.
The basic functionality of the scripts is as follows:
- Searches for all running and not running instances of a software
- The properties of the found software instances are read out (including version number, installation paths, etc.)
- The compliance checks are executed for each instance
The scripts can also be extended with additional functionalities, such as searching for active user accounts.
Module 3.2 – Deployment of the Compliance Checks
The compliance checks are distributed to all servers. This can be done automatically via Ansible or other tools you use.
Module 3.3 - Execution of the Compliance Checks
Compliance checks should be carried out regularly - ideally once a day. This can be controlled by a CRON job, for example.
When executing the scripts, the following is performed, depending on the software:
- Collect all server information (operating system, ...)
- Search for all active and inactive instances of the software
- Reading of the instance properties, such as version number, installation paths, configurations and much more
- Execution of the compliance checks per instance found
- Execution of further functionalities, like the search for user accounts in the software, ...
- Storing the information on the server, or transmitting the data to a central database
Module 3.4 – Collect and store the compliance check results
The compliance check results must then be collected from all servers and stored in a central database.
Module 3.5 – Compliance Check Reports
The compliance reports relevant to your company can then be created from the database.
IT Compliance